Wpa Enterprise Vs Personal
Two Modes of WPA/WPA2: Personal (PSK) versus Enterprise. Both versions of Wi-Fi Protected Access (WPA/WPA2) can be implemented in either of two modes: Personal or Pre-Shared Key (PSK) Mode: This mode is appropriate for most home networks—but not business networks. You define an encryption passphrase on the wireless router and any other access. WPA2 Personal uses pre-shared keys (PSK) and is designed for home use. However, WPA2 Enterprise is specifically designed for use in organizations.Benefits of WPA2 EnterpriseThough WPA2 Personal is easier to deploy and use than WPA2 Enterprise, it is not the most secure option and should be used just as the name infers, for personal or home use.
Quick Summary.Why it’s important to know about these protocols?All these wireless standards have been created to keep your home network safe. Each of these protocols has their own advantages and disadvantages. It’s up to the user to select a suitable protocol. This article is exactly about knowing which protocol to use at which time.One thing to keep in mind is that the wireless technology is inherently insecure as we can’t control the spread of wireless signals in the air. That is why it’s important to select the best security protocol which will minimize the risk of being hacked or data leakage. WEP vs WPA vs WPA2 Personal vs WPA2 EnterpriseInstead of discussing about each security protocol, we will discuss about three factors and compare the protocols according to these factors. The factors include security, authentication and performance.
Security and EncryptionWEP and WPA use RC4 algorithm for encryption of network data. RC4 is inherently insecure especially in case of WEP which uses small keys and key management. Since WEP sends passwords in plain text across the network, it is quite simple to crack the network using network packet sniffers.WPA was developed as a temporary alternative to WEP. The secure form of WPA uses TKIP encryption which encrypts passwords for network communication. Although it is also weaker form of security but it’s far better than WEP.WPA2 was designed for network communication with complete security in mind.
It uses AES-CCMP encryption which theoretically may take hundreds of years for cracking. All communication packets sent and received through WPA2 are encrypted.While WPA2 is the best form of security, you may use WPA where devices are not compatible with WPA2 and use WEP as a last resort as it is still better than the network being completely open. AuthenticationAuthentication is an important part of wireless network communication. It determines whether a user is allowed to communicate with the network or not. All three security protocols, WEP, WPA and WPA2 use (Pre-shared Key) for authentication. While WEP uses simple PSK key, WPA and WPA2 combine it with other encryption methods like WPA-PSK and EAP-PSK to make the authentication process more secure. The standard which WPA and WPA2 follow for authentication is 802.1x/EAP.
WPA and WPA2 use 256-bit encryption for authentication which is quite secure. But since the users tend to have difficulty setting such a long passwords, the passphrase can be between 8 and 65 characters which is combined with EAP for encryption and authentication. Speed and PerformanceThe first thought over speed and performance is that since WEP uses simple authentication and security, it should be the fastest. But this is totally different from the factual figures. Instead of using more encryption and security, WPA2 seems to be the highest performing security protocol of all. This is because it allows more bandwidth to be transferred between the Wireless Access Point and wireless device. You may check out the following video which explains about an experiment of comparing speed and performance of these three protocols, WEP, WPA and WPA2.
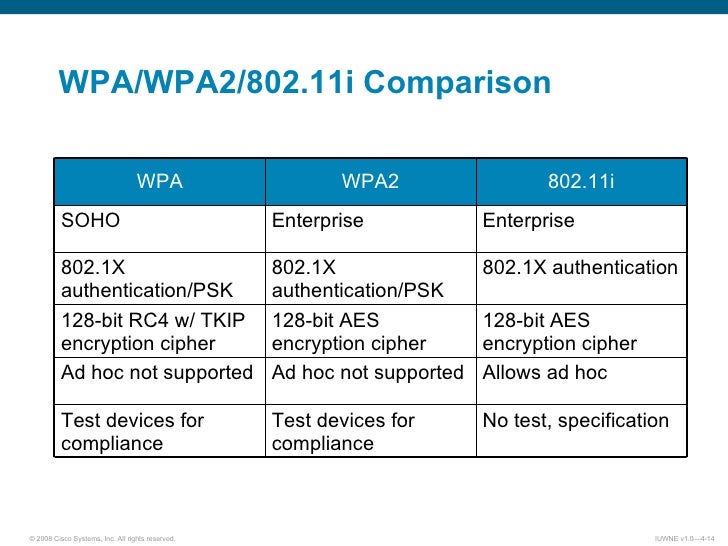
WEP, WPA and WPA2 Comparison TableHere’s the comparison table for you to easily check the differences between WEP, WPA and WPA2 ProtocolEncryptionAuthenticationWEPRC4PSK 64-bitWPARC4 and TKIPPSK 128 & 256 bitWPA2AES-CCMPAES-PSK 256 bitConclusionMy final verdict is that if you have a modern device, you should almost always use WPA2 and good encryption and authentication algorithms as this will make your wireless network more secure. But if you have an old device which does not support WPA2, then you should go with WPA with high encryption and authentication. The third option is to go with WPA and relatively low quality encryption and authentication. I would suggest WEP as a selection of last resort as it’s still better than keeping the wireless network wide open without security. Must Read Articles:.

Wpa2 personal uses preshared passphrases to connect various devices to the wireless network; this is probably what 99% of all home users use. The wireless device takes your preshared key and hashes itwith your ssid name and sends the information via a 4 way handshake to get the current encryption keys and these keys change at regular intervals (default 1 hour)im not 100% sure on this one. But this is the impression i get.wpa2 enterprise relies on an authentication server, and i believe each cient is given a different encryption cipher or the server is the one that has the keys and gives the current keys to the client. The cient does not use a preshared key. The only time i ever used wpa2 enterprise was google secure wifi in mountain view.
Wpa2 Psk Vs Wpa2 Enterprise
How does one setup the RADIUS authentication server on their Mac Pro. Also I don't think there is ever a reason a home user shouldn't be recommended to use something a computer can do. How do you know what I need at my home. This isn't an answer to the question its an assumption and the same amount of information I could derive from reading the Airport Utility.app fields.

Wpa Enterprise Or Personal
You just wasted your hands typing that and I need a more secure wifi connection from all the hackers living in the college accross the street. As far as WPA2 enterprise goes it sounds perfect for my uses so can someone please explain usinging this to all us Airport home users and stop assuming things. Apple Footer.This site contains user submitted content, comments and opinions and is for informational purposes only. Apple may provide or recommend responses as a possible solution based on the information provided; every potential issue may involve several factors not detailed in the conversations captured in an electronic forum and Apple can therefore provide no guarantee as to the efficacy of any proposed solutions on the community forums. Apple disclaims any and all liability for the acts, omissions and conduct of any third parties in connection with or related to your use of the site. All postings and use of the content on this site are subject to the.